py kaam karny ki zarorat hai,
ye 1 simple or easy job hai, jisy har koi ba-asani kar sakta hai. Ye 1 investment job hai,
is job ko wo dost bhi kar sakty hain jin k pas internet nahi hy,
is job sy ap apny or apni family or apny doston k halaat badl sakty hain,
jo log ye nahi manty k internet sy paisy kmaye jaty hain unko ap dikha sakty hain k ab sab kuch mumkin hy,
· No need for Team Work
· No need for Time limit
· No need for daily work
Is job main ye system nahi hy k jab tak ap k downline koi referral nahi aye ga tab tak apko paisy nahi milen gy,
balky is job ka faida ye hy k bina kisi referral or bina kisi roz k home work k bagher apko daily income milti rehti hai.
Is main aap ney bas invest karna hy or us investment ka2% hissa roz apko mila kary ga.
For Example !
Agar aap ny $100 invest kia hai to uska 2% hissa jo$2 banta hai wo daily apko mila kary ga.
Or agar aap chahty hain k apki roz ki income zyada ho jaye to ap or zeyada invest kar k apni daily income barha sakty hain.
Aam Sawalaat…
Q: hamein ye 2% hissa kab tak milta rahy ga? Kya iski koi limit hai???
Ans: G han, har position ki limit 75 days tak hai, After 75 days position expire ho jaye gi. after then apki choice hogi k ap or profit kamana chahty hain k nahi.
Q: kya hamein har baar apni jaib sy invest karna parhy ga???
Ans: nahi. Company sy jo dollars ayen gy ap usi ko wapis invest kar k bhi apni daily income barha sakty hain.
Q: kya koi referral downline lgany ka koi faida hoga???
Ans: G HAN, ap apny downline referral laga sakty hain or unka faida bhi hoga.
Q: referral ka hamein kya faida hoga???
Ans: apka referral jab bhi koi position ly ga to uska apko $1 bonus mily ga.
Q: Position kya hai???
Ans: is main $10 ko 1 position kehty hain, or har position ka $1 bonus apko mily ga.
Q: kya hamein referral k referral ka bonus bhi mily ga???
Ans: G Han, bilkul apko ap k referral k referral ka bonus bhi mily ga,
Ap k referral ka referral jb bhi position ly ga to uska0.50 Cents bonus apko mily ga.
Remember that apko bas 2nd referral tak bons mily ga 3rd referral ka bonus apko nahi mily ga.
Q: kya hamary referral ka bonus bhi hamain daily income k sath milta rahy ga???
Ans: Nahi, ap k referral ka bonus apko bas us waqt hi mily ga jab wo koi position ly ga. or jab tak wo position leta rahy ga apko har position ka bonus milta rahy ga.
Q: Kya humary referral ki koi limit hogi???
Ans: Nahi, koi limit nahi hogi. Ap jitney chahen referral laga sakty hain.
Q: kya hamara account har roz login hona zarori hai???
Ans: Nahi, ap jab chahen login kar sakty hain. chahen to 75 days bad login kar len. apko apka profit complete mily ga.
I hope apko ye job pasand ai hogi or ap is interesting or easy job ko karny main dair nahi Karen gy.
Daily Incom Chart
Join karny ka tarika.
Step by step…
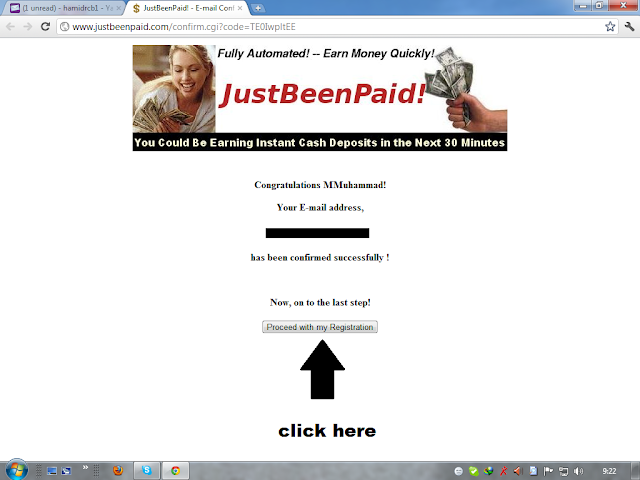
Pehly ap is link ko open Karen,
Step 1: joining page open karny k bad,
Step 2: Sign up karny k bad apko email bheji jaye gi jis main apka account active karny ka link bheja jaye ga.
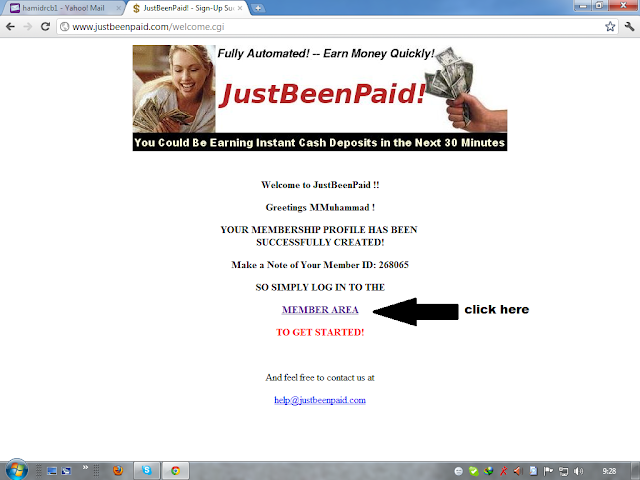
Step 3:
is
step k bad apko 1 member i.d dia jaye ga jo is pic me bna hua hy. like
268065. or jo apko member i.d mily ga usy yad rakhiye ga because us
member i.d k bagher apka account login nahi hoga.
Step 4:
Step 5:
Step 6:
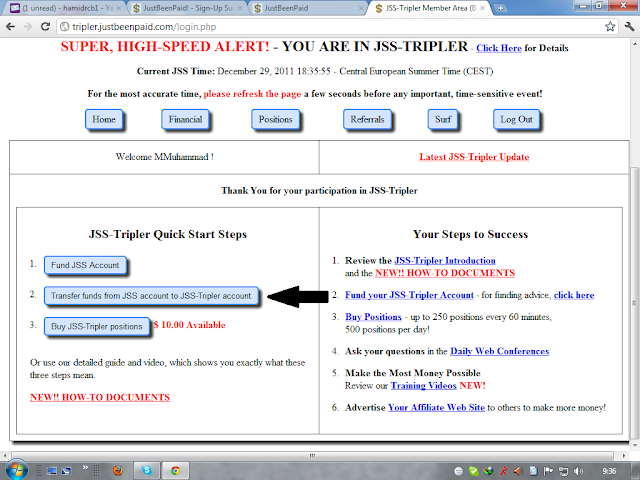
Account login karny k bad Jss-Tripler py click karen.
Step 7:
Step 8:
Step 9:
Step 10:
Step 11:
Step 12:
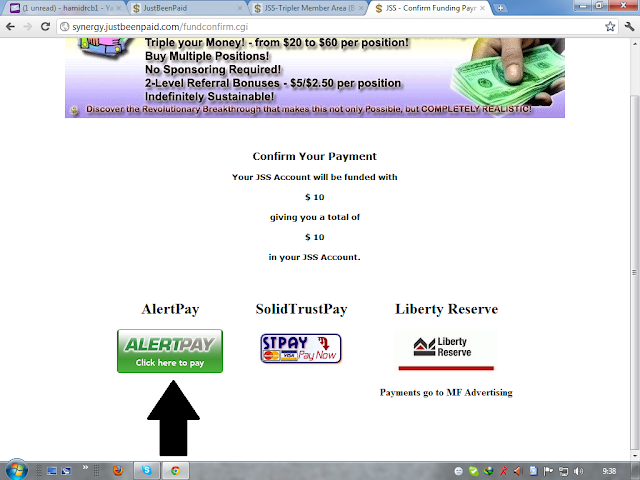
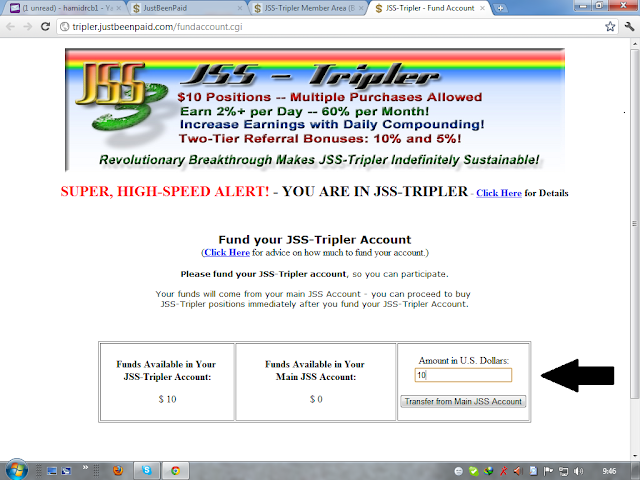
now ap apny account sey dollar invest karny k liye is option Fund JSS Account ko open karen gy.
Step 13:
Ap
jitny dollar invest karna chahty hain wo is khali box me likhiye. for
example agar ap $10 invest karna chahty hain to 10 likhen.
Step 14:
After then ap apny jis account sy dollar invest karna chahty hain us py click karen,
Step 15:
apna AlertPay ka email or password likh kar login karen.
Step 16:
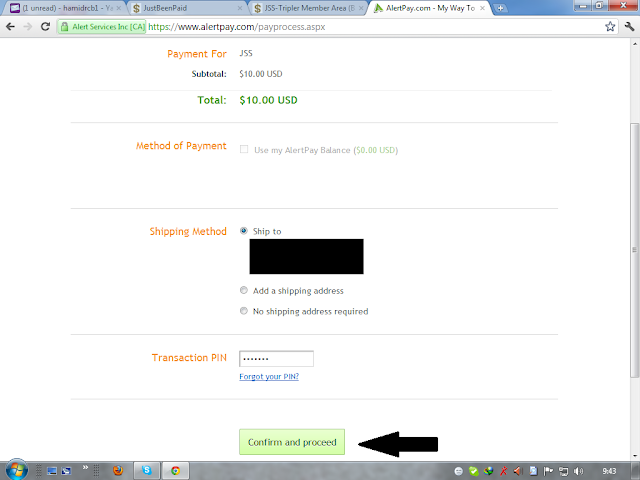
Step 17:
Confirm
and Proceed karny bad ap k dollar JSS k Fund account main chalen jayen
gy. phir ap wo dollar ap apny JSS k fund account sy JSS-Tripler account
main transfer karen gy.
Step 18:
Remember that ap ne jitny dollar AlertPay sy JSS-fund main invest kiye thy wohi is jaga main likhen. masln ap ny $10 diye thy to khali box main 10 likhen.
Step 19:
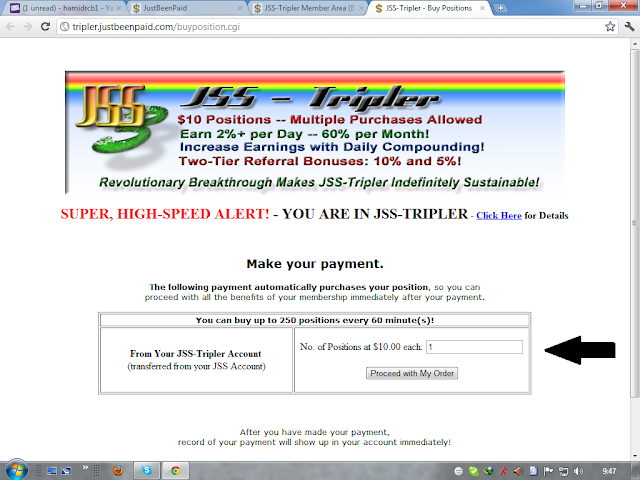
Now your last step. ab ap ny Buy Jss-Tripler position ko open karna hy.
Step 20:
yahan ap apni positoin ka number likhen gy. agar ap 1 position lena chahty hain to is khali box main 1 likh k proceed kar den,
Step 21:
Step 22:
Confirm karny k bad apka account puri tor py ready hai. ab apki daily income start ho gai hy.
Step 23:
Now complete your steps…
Ab ap apni earning aglay din dekh sakty hain.
apni Financial option ko open karen or apna daily profit dekhen.
date and time k sath apni earning dekhny k liye page k last me ajayen,
http://www.justbeenpaid.com/join.cgi?r=raka&p=&c=